Setting up Azure AD Sync
In a few previous posts, I’ve set up an on-prem Active Directory environment and done a few things in there. In this post, I’ll be turning it into a hybrid environment with the aid of Azure AD (or as it sometimes likes to be called, Entra ID).
So, before you read this post please be aware that I already have an on-prem domain controller with all the basic services setup – you can see how I did that here.
This will require an Azure account, which can be created for free and includes a free trial with $200 worth of credits to use in 30 days. As seen above, my dashboard is rather bare.

We will begin by navigating to all of the various resources which can be created within Azure.
Whilst there’s plenty of options, the only one I need for this post is Microsoft Entra ID.
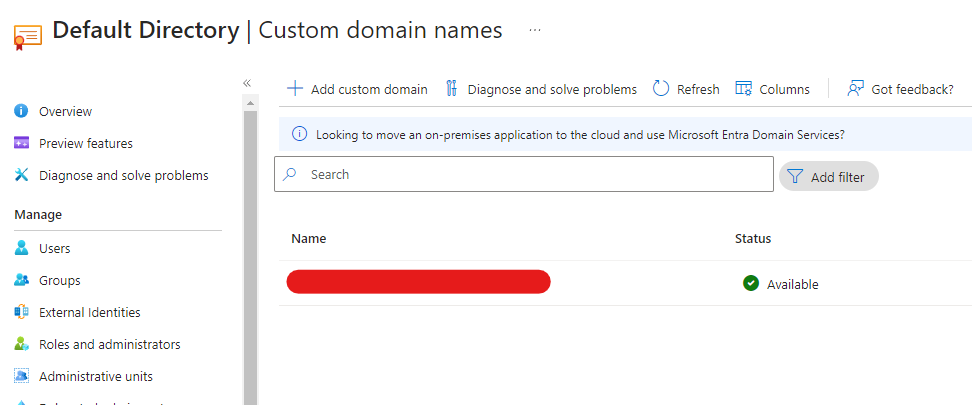
The first thing I want to do is create a custom domain name. This is because the one automatically created for me includes both my personal email address and it is incredibly long. Plus, I own the zenfulmonkey.com domain and it’d be a shame not to use it. So, I’ll click the ‘Add custom domain’ and get started.
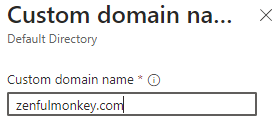
The first step is easy: type in the name of your domain.
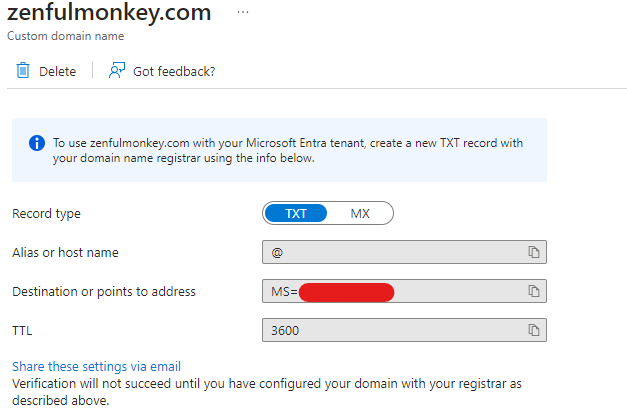
Next, we are given a DNS record we need to create within our DNS registrar. If you’ve read my other blog posts – you will know I use Cloudflare for my DNS.
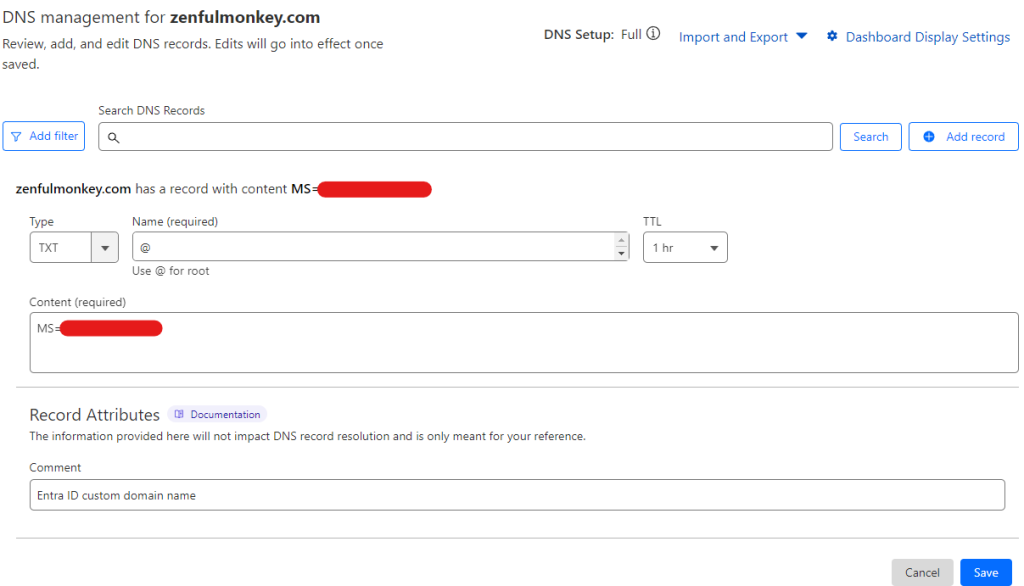
This is a pretty straightforward step. Simply go to Cloudflare (other DNS registrars are available), and fill in the details.
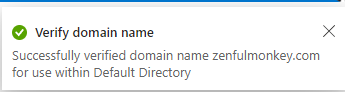
Azure handily provides a feature which allows you to verify that this DNS record has been properly configured – which it has. Our custom domain name is created.
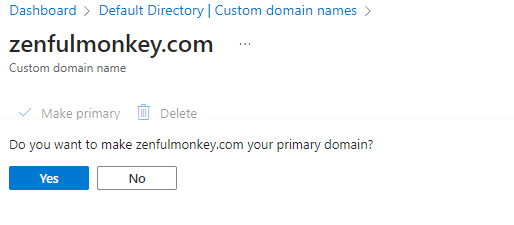
We can then navigate back to the Custom domain names section, select it, then make it our primary domain name. Please note that you won’t find this referenced throughout the rest of the post – this was a later addition I found and hastily added in afterwards.
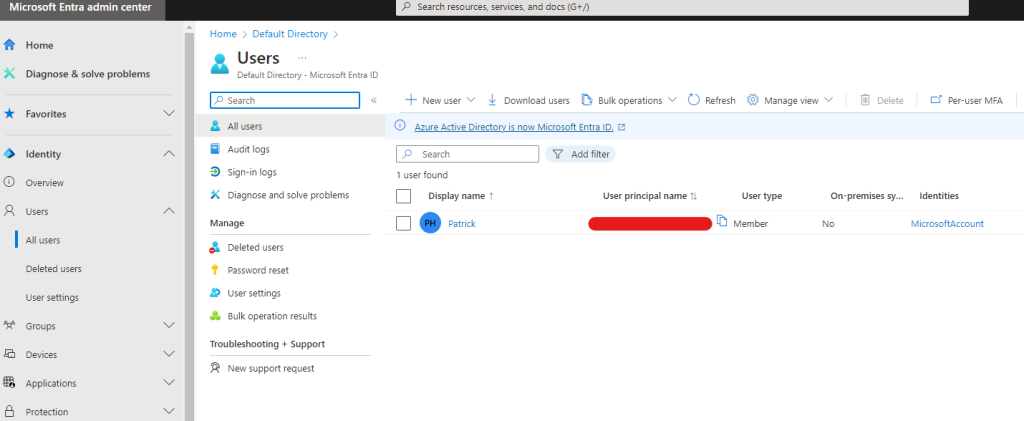
Next, I’ve headed to the Microsoft Entra admin center, where I’ve seen the rather bare ‘Users’ section. Our goal is sync this with our on-premises environment and be able to manage our on-prem users from the Microsoft Entra admin center. This information can also be viewed from the Azure admin center, but I thought I’d switch things up a bit and familiarise myself with both UIs.
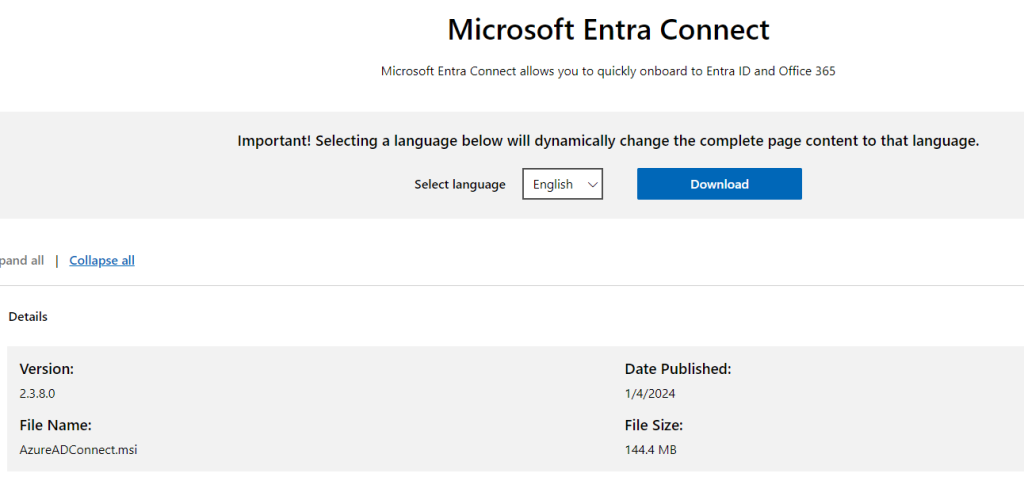
Here is Microsoft’s official download page where you can download the Microsoft Entra (Azure AD) Connect tool.
Now, the easy thing to do would be to navigate to this website whilst on my domain controller VM and download it straight onto the correct machine. However…
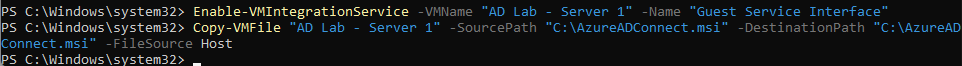
I like to do things the hard way occasionally, so I downloaded it onto my host machine and then used PowerShell to transfer the file onto the VM.
And here’s the installer, ready to run.
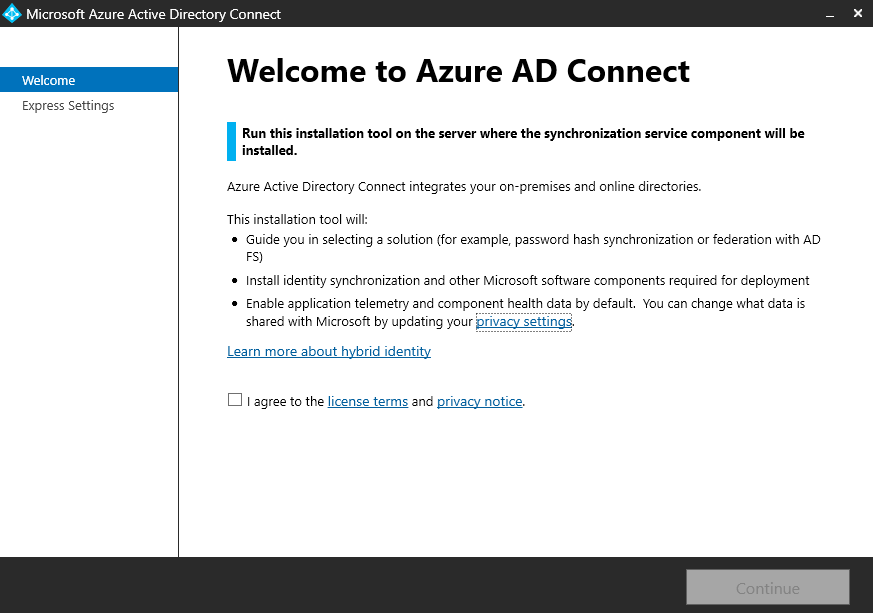
Once installed, we get the Azure AD Connect tool which we can now run to configure the syncing between our on-prem environment and our cloud environment.
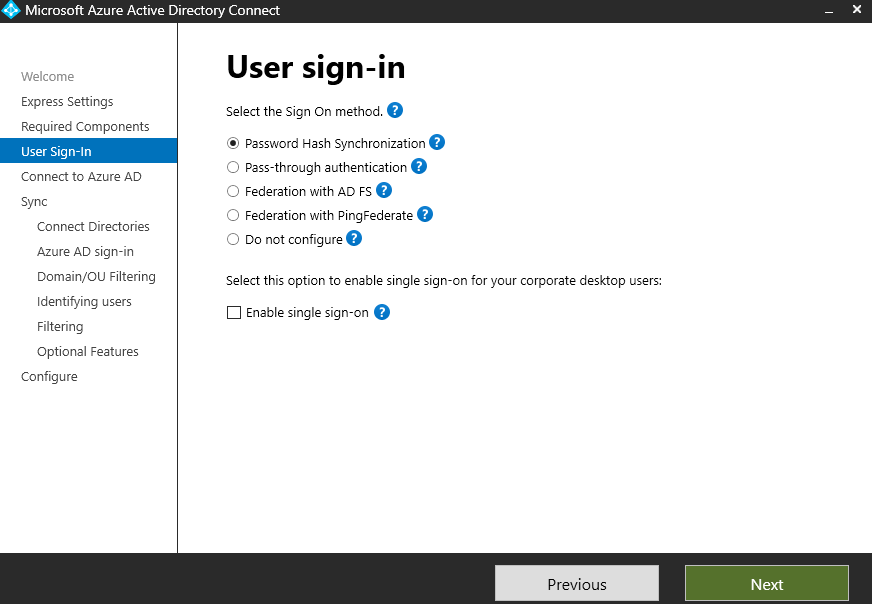
I’ve decided to use Password Hash Synchronization. In all honesty, it’s because it seems to be the simplest option.
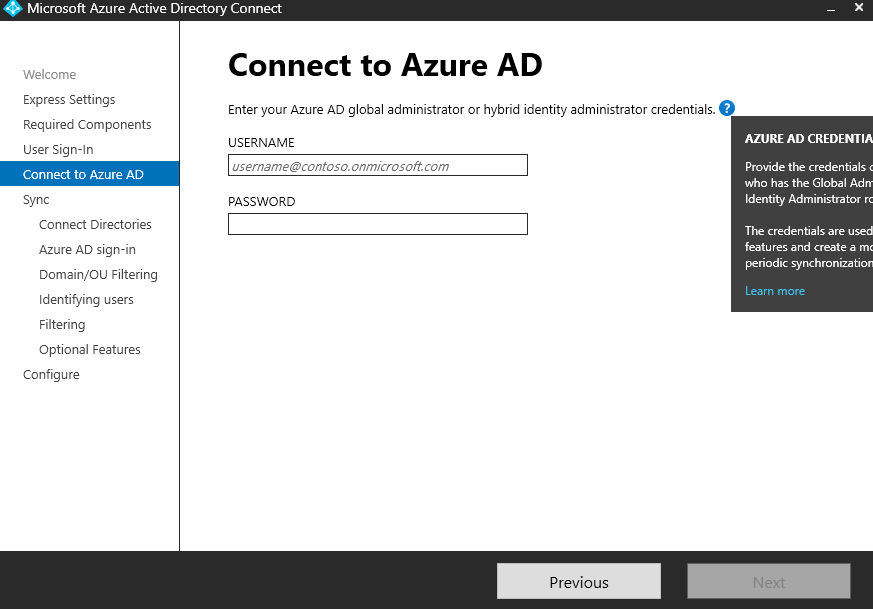
I’m now prompted to connect to Azure AD using one of my Azure AD administrator accounts. This is as good a time as any to actually go through creating a user within Entra ID, so I’ll create myself a global administrator account.
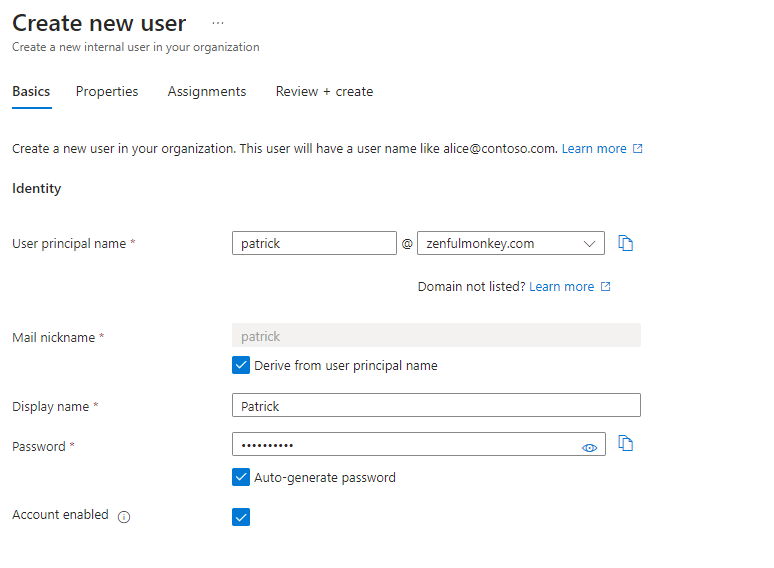
Here’s the account details filled out, and I even got to pick my beautiful custom domain name.
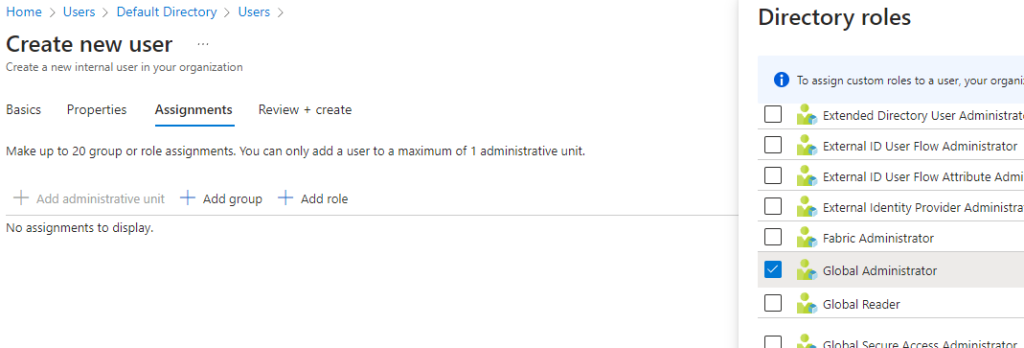
I’ve also assigned this account the role of Global Administrator so it can be used to authenticate me using this tool, and I’m sure it will be handy later too.
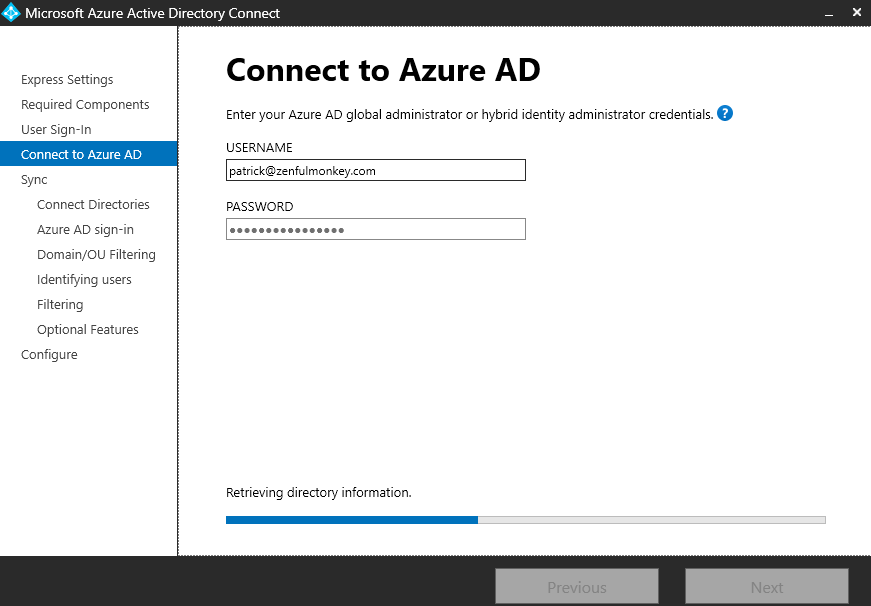
After quite a lot of issues, which I’ll spare you the details of, I got things working and the connection began.
Up next was to connect my on-premises directory forest. For this, I needed to log in using one of my on-prem accounts. So, I ensured that my administrator account was a member of the ‘Enterprise Admins’ group and used it to log in:
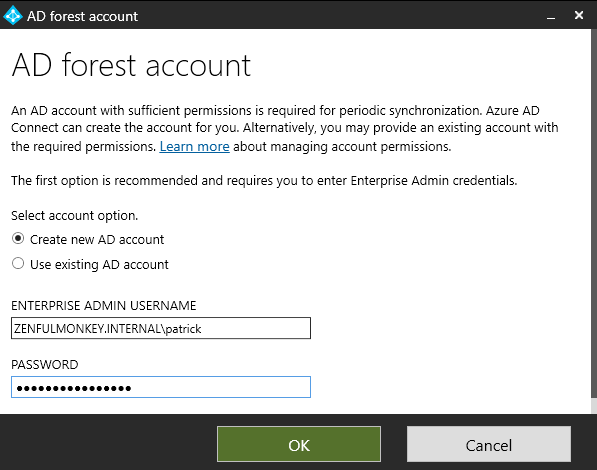
Here, I’ve selected the option of creating a new AD account for the sole purpose of syncing the two environments. Whilst using an exiting AD account wouldn’t be an issue for my setup, it’s not something you should do whilst in a live environment. What if the admin account that you use for this is disabled by someone for some reason? What if the admin account belongs to a member of staff who then leaves, and it HAS to be disabled but it will then cause issues for your AD sync?
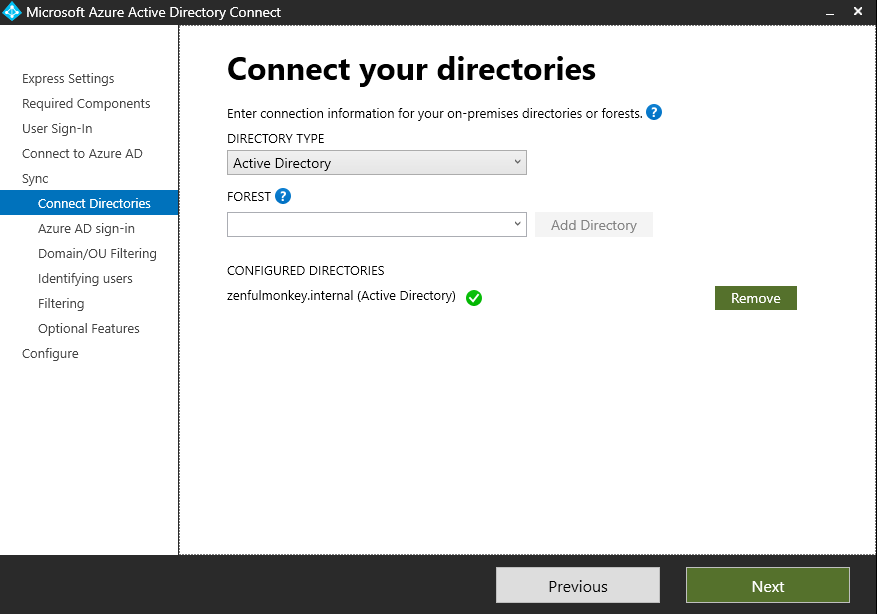
The Azure AD Connect gives me a little tick next to my directory to show that it will be synced, and we can continue.
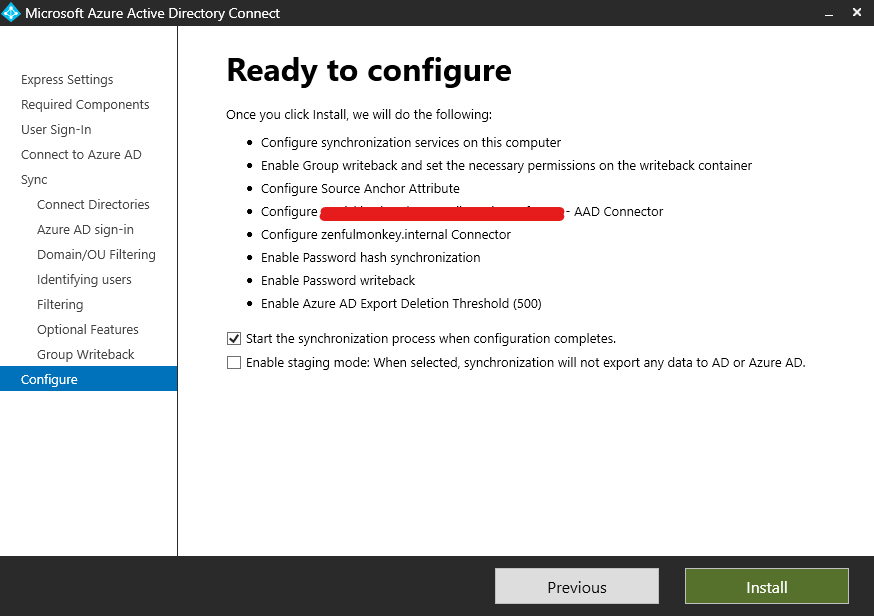
I’ve skipped over a few of the configuration pages here as the majority of them I’ve just gone with the default settings for. We can now click ‘Install’ and wait patiently as it does so – it does take a long time.
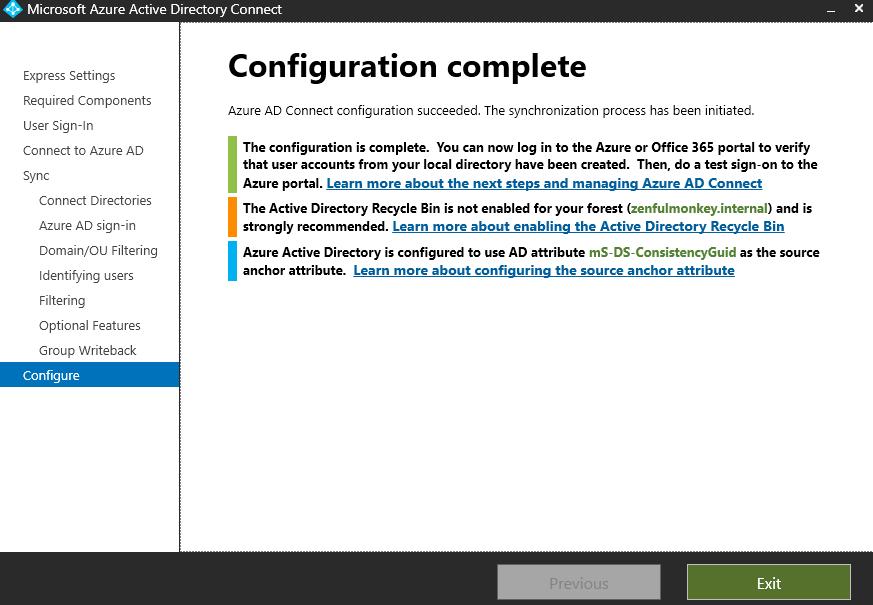
The configuration is complete. Now, let’s see if our on-prem users have been synced to Entra ID.
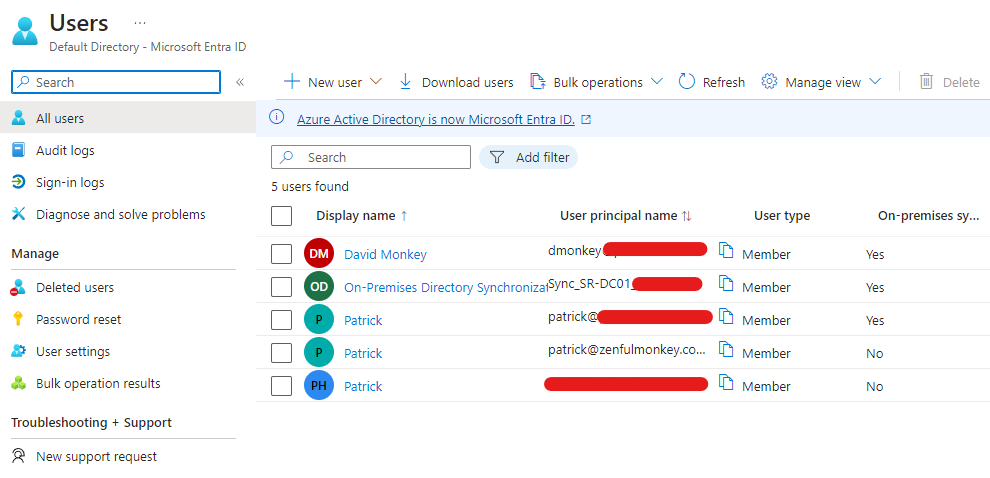
Refreshing the ‘Users’ page now shows that I have three more users, and in the column on the right you can see that they are from an on-premises sync.
So, that’s the basics of the Azure AD Connect tool, which has allowed me to create a hybrid environment. Thank you for reading.

Leave a Reply